Authenticating the Special Operations Manual
By
Dr. Robert M. Wood
Introduction and Background
“Any sufficiently advanced technology is indistinguishable from magic.” These words by Arthur C. Clark reflect what I believe: there is no magic. There are secrets, but they are the secrets of science and technology. During my professional career, I had been hungering for the opportunity to really probe into the technology of UFOs, and so when I retired in 1993, I was ready for the Special Operations Manual challenge.
Slide 2. During my career with McDonnell Douglas, I led a little project aimed at gravity control and had become well acquainted with Jim McDonald, who talked me into visiting the Condon Committee. I “retired” in 1993, and Stan Friedman had been given some poor copies of a “manual” with the fascinating title of “Extraterrestrial Entities and Technology—Recovery and Disposal.” He put me in touch with owner Don Berliner, who graciously went with me to a copy shop and I made very high quality copies from the original negatives, which is what Don had received in the mail. Today, I will be summarizing the content of this remarkable document, discussing its provenance, analyzing its authenticity, rebutting claims of fakery and telling you my latest thinking.
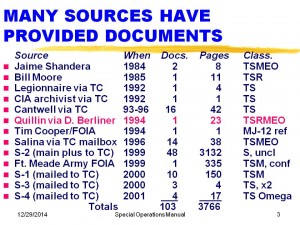
Slide 3. We begin with a summary table of the various documents I have obtained from a variety of sources, totaling over 3500 pages, of which more than 600 pages are top secret. This table shows the source, the date it was leaked, the number of documents obtained, the number of pages, and the classification. M means code word MAJIC, EO means Eyes Only and R means Restricted. The next table (Slide 4) gives the name of the principal documents for each source. However, today we are primarily looking at the Special Operations Manual received by Don Berliner, mailed from Quillin’s Drugs in La Crosse, Wisconsin.
Before we get to the Manual, I wish to establish a relevant background shown in Slide 5. Everyone who has studied the topic agrees that the US awareness of the flying saucer problem started with Kenneth Arnold in June 1947, followed by the Roswell crashes (there were at least two). In 1950, Paul Trent took a photo that had a shape that was identical to one photographed in France in 1954, and in 1952, overflights of Washington caused the Robertson panel in 1953 to reduce public attention to this topic. In 1954, there were large numbers of interactions in France, with a spate of over 200 landings and 35 humanoid reports.
Slide 6. However, documents leaked to Tim Cooper from S-3 and others on Slide 4 revealed that there was a crash Cape Girardeau, Missouri in 1941, and we have interviewed the granddaughter of the minister who was called out to “bless the bodies.” After the famous “Battle of L.A.” there were two craft recovered—one crashed in the San Bernardino Mountains, and one was salvaged at sea by the Navy, according to leaked documents from Marshall’s correspondence. The significance is, of course, that if we had recovered such alien craft in 1942 we would have had much more time to put our security plans in place in detail, including procedures to be used if other crashes occurred. This logically gives rise to the need for a recovery manual of some sort. We seem to be in possession of a 1954 edition, which is what this whole presentation is about.
The Manual arrived by US Mail as a roll of undeveloped 35-mm Tri-X film that—interestingly—was manufactured in 1954. It came in a green box (Slide 7), hand addressed to Don Berliner using the same format that was provided for his contact in his MUFON  presentation of July 1989. Postage was paid by an Fmeter number 2223773 made by Postalia, and issued for use by Quillin’s Drugs in La Crosse WI. Postmarked March 7, 1994.
presentation of July 1989. Postage was paid by an Fmeter number 2223773 made by Postalia, and issued for use by Quillin’s Drugs in La Crosse WI. Postmarked March 7, 1994.
These bullets (Slide 8) hit the main points: it is a Special Operations Manual (hereafter shortened to Manual) with a classification of Top Secret and code word of MAJIC, not to be retained (EYES ONLY). It is printed on one side with a security warning notice on the facing pages. . It was, after developing, printed as 5×7 images, two per 8.5 x 11 sheet. In 1995, I began, from the best copies I had, to create a replica—primarily with the objective of just reading the words because it was so hard to read. Using the high quality copies made later has resulted in a nearly complete reconstruction of every word in the Manual, and this is what I will now rapidly summarize in the next 29 slides, highlighting items that I have found to be of special significance.
Before we begin, it is important to realize that IF you are satisfied that we might have had several recoveries prior to 1954, that it is quite logical that a manual of instructions should have been produced. So, some of you may be asking, “How do I know this is not a fake?” I will discuss this issued in more detail later, but in the meantime, you could logically have the view that if such a manual is likely to exist, it is not worse than a 50/50 chance that this is a fake. Typically, strong arguments of fakery come from those who have had access to classified material in their careers and see aspects of this Manual that do not coincide with what they have been told the security regulation would have been. None of these critics had Top Secret code word clearances in 1954. Furthermore, this project was clearly viewed to be so critical that they could have had the influence to create their own security regulations.
What the Manual says
 This Slide 9 summarizes some of the main highlights of the Manual: purpose of recovery with secrecy, acceptance of extraterrestrial origin, huge emphasis on keeping the public uninformed, and very practical crating and shipping instructions. Of special note: included are some instructions for UFOB (Unidentified Flying OBject) reporting that are identical to an unclassified version, and the specification of arcane references to be precisely the ones for the 1954 time frame.
This Slide 9 summarizes some of the main highlights of the Manual: purpose of recovery with secrecy, acceptance of extraterrestrial origin, huge emphasis on keeping the public uninformed, and very practical crating and shipping instructions. Of special note: included are some instructions for UFOB (Unidentified Flying OBject) reporting that are identical to an unclassified version, and the specification of arcane references to be precisely the ones for the 1954 time frame.
The cover (Slide 10) is quite an attention-getter, with the title, “Extraterrestrial Entities and Technology—Recovery and Disposal” telling the story of what the Manual is about succinctly. It does have a Restricted caveat along with the Top Secret ones on the cover only. This anomaly will be discussed later. The War Office Logo was used whenever the customer wanted it used (according to the US Government Printing Office) all the way up to 1969. The footnote imprint identifies not only that fact that MJ-12 was the customer but the jacket and job numbers provided during production. The Manual is issued as a TO or Technical Order, and there is a sophisticated assignment of numbers and letters available in the archives at Tinker Air Force Base. The 12, for example, denotes avionics.
The use of a security warning facing every page (Slide 11) is uncommon but not unique. Some have claimed that permitting the “widow” word “forbidden” on the last line proves that it was not produced professionally. However, the USGPO Style Manual only requires “widows” to be eliminated when they cost an extra page and therefore money. Numerous examples of widow lines exist in authentic manuals.
After the Table of Contents (which follows in exact detail every capitalization, punctuation, spacing and italicization noted in the Style Manual and confirmed by comparison with manuals of the era), we have the purpose and goals shown in Slides 12,13,14 and 15. You can see obvious desire to “increase efficiency of future operations” (did they have earlier disaster such as Roswell?); focus on “the very highest national security”; kickoff by Forrestal and V. Bush. Slide 14 identifies the six specific goals, including running secret locations, recovery “anywhere in the world” and absolute top secrecy. Slide 15 talks to the “current situation” of April 1954, assessing the ETs as a small threat compared to that “from unfriendly powers.”
Slide 16 scopes the content of the rest of the Manual, identifying a list of personnel in Appendix II that is unfortunately not photographed, or perhaps not included in the photographer’s copy.
Slides 17, 18, 19, 20, 21, 22, and 23 provide definitions and data, starting with extraterrestrial technology including any material exhibiting characteristics “beyond science” and extraterrestrial biological entities (EBEs) as clearly different from homo sapiens evolution. The craft are described with a range of dimensions, ports, lights, landing gear. They are shown in Slide 19 with the fingers of the photographer. The ice cream cone shape more or less resembles that reported in the famous Cash-Landrum Texas case resulting in personal injuries. Slide 20 presents the dimensions and notes that “Air Force and Central Intelligence” are the source of the data based on wreckage collected from 1947-1953 inclusive. This would be consistent with the Air Force and CIA not having access to the prior crashes, which may have involved the Army, FBI, AEC and Navy.
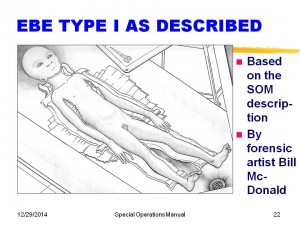
Slide 21 provides a detailed description of EBE Type I, and Slide 22 is Bill McDonald’s forensic rendition of these data. Bill has provided these drawings based not only on the information in the Manual, but much experience and exposure to historical autopsy procedures, tables and equipment, together with sources such as Leonard H. Stringfield who had witnesses providing confirming descriptions.
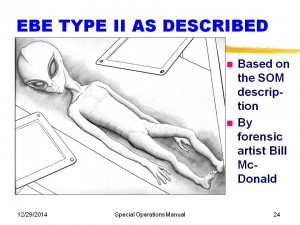
Slide 23 gives the EBE Type II description, and Slide 24 is Bill McDonalds forensic rendition. The cranium ridgeline is described in the Manual as “a slight peak that runs over the crown.”
Finally, Slide 25 defines and describes extraterrestrial technology including materials “not known to Terrestrial science” and with great strength not obtainable then. The Manual in effect concedes that we do not know how they are made or what they are made of.
After the Introduction and Definitions, guess what comes FIRST? Security! Section 12 on press blackout makes it very clear that virtually any deceptive step is fair, whether it is official or unofficial, true or false, ethical or unethical—and by inference—legal or illegal. This includes telling people there has been a “downed satellite” or a toxic spill—whatever sells.
Later, we will discuss the point that the first known successful satellite was in 1957. Clearly, Section 13 shows that they had a rather specific plan for securing the area, establishing a perimeter, secure communications, absolute “debriefings” to keep the individual silent about this up till their death beds.
Slide 27 shows an enlargement of the exact words used for deceptive statements. It also shows, in the penultimate line on the right, that the “z” character is slightly raised from the rest of the text. Later, I will describe this as a very significant indicator of the use of a hot lead printing press. This is contrasted with a modern attempt at hoaxing the anomaly of occasional raised “z”s found in conjunction with the use of Monotype presses.
Slide 28 describes the procedures for moving the parts, with the RED TEAM assigned to complete craft, and OPNAC in charge of any EBEs dead or alive. Again, security plans to “remove all traces” of any crash. This is why it is so difficult to find traces today even if we find the right crash site. The Manual alludes to a Contingency Plan in the event that large segments of the public and press witness the craft. Such a plan was also noted as Attachment G to the Eisenhower Briefing Document. Has this plan ever been put into effect during mass sightings? Interesting to wonder this.
Slide 29 is the actual content of one of the Manual pages, the Extraterrestrial Technology Classification Table. It categorizes all items into eleven categories, gives them a code name and says where to ship each kind. This table raised a red flag in some quarters because it identified “Area 51 S-4” as one of the receiving facilities. Later, we will provide evidence that this facility was started under construction in January 1951.
Slide 30 describes the paperwork process to ensure proper accounting, essential so that nothing gets lost or in public hands.
Slide 31 details the procedures for packing and associated paperwork. One expert on shipping paintings has volunteered that the procedures identified are consistent with the very best procedures then currently in use in the art world. The identification of Kraft tape as a shipping tape is right for the 1954 period. This tape is now not widely known, having been apparently replaced by the use of duct tape that requires no moisture. It emphasizes again that organic matter (EBEs dead or alive) is handled differently.
Slide 32 deals with receiving and handling, again with detailed thoroughly professional directions for ensuring safe removal of contents, complete with packaging diagrams. Two small anomalies are here: first, the words screw driver are separate as they were in 1954. Second, the word dessicant is misspelled, but it should be desiccant, an error that would be made by many today. The fact that this is the only error in the Manual suggests that it went through a detailed USGPO-like proofreading process but was not checked with a spellchecker; mine picked out this mistake right away.
Slide 33 explains our policies very clearly with respect to EBEs: they do not exist, no agency is investigating, cover stories will be ready.
Slide 34 reaffirms that OPNAC is in charge of the EBEs, and that they are to be captured and removed to a secure location by “whatever means are necessary.” “Loss of EBE life is acceptable.”
For non-living organisms, shown on Slide 35, the focus is on retrieval and preservation, while minimizing contact with them and marking them.
Slide 36 identifies the kinds of references that the Manual provides. These references have been checked against those applicable and found to be consistent with the document numbers of the era; furthermore, similarly dated authentic manuals use some of the exact same references.
The Manual includes a handy guide to UFO identification and is summarized on Slides 37, 38 and 39. These words are identical to those that were in internal review by the Air Force. They include some interesting criteria, such as at least 1/4-minute of observations, more credibility with multiple witnesses, and follow-up proportional to inverse square of distance. It notes that if it is older than seven days it is not likely to be of value. It also emphasizes the value of photos, material or hardware. (Obviously to be taken from the witnesses where possible.) Slide 39 summarizes the five kinds of normal stimuli that account for most of the misperceptions of conventional objects or lights. About a dozen considerations are offered for each of these five stimuli.
Authentication Techniques
The techniques for authenticating questioned documents are not mysterious. They are tried and true, and used by professionals all the time for legal or copyright issues. Slide 40 summarizes the main techniques. Clearly, establishing provenance is a very helpful event. If documents were genuinely classified and then “leaked,” this action is illegal (as the security warning notes), and so the leakers attempt to conceal their identity, as is the case for the Manual. This unfortunately breaks the provenance chain of custody.
Moving to the physical processes, with original paper, it is possible to date the ink, identify the watermark and the paper. For typewriter impressions on original paper, it is usually possible to compare with a library of fonts and identify the typewriter make and model. None of this applies to SOM 1-01 since it is printed. There, however, we can identify the type fonts used and we will touch on that in a moment. The Manual has no signatures.
Intellectually, we can hunt for anachronisms, compare language usage and compare with other known authentic documents. Although not shown, it is also possible to use forensic linguistics to identify the precise writing style of one individual. This would seem to have low value if the document was created by committee.
Slide 41 gives a beautiful example of great provenance with the Bowen Manuscript received from an FOIA office at Ft. Meade. The originals were identified to be old, and written by Vernon Bowen. I was able to locate his son, who has confirmed that his father wrote this documents. Excellent provenance.
Slide 42. As far as SOM 1-01 goes, the provenance begins with Don Berliner receiving the box and its contents of exposed 35-mm Tri-X film. The meter, however, provides a clue and we have identified Quillin’s Drugs as the source of the meter, and members of the Quillin family and one of the employees has been interviewed. One researcher has claimed to have held the Manual that was photographed in his hand and noted that it was “old paper.” The fact that the film negative was manufactured in 1954 suggests that the photos might have been taken as early as that. However, I am not sure who has the Manual now and it would not be constructive to speculate. I suspect that it is still in La Crosse WI. If the owner would voluntarily loan it for inspection, it would end a lot of guessing. Furthermore, since the contents have been publicly disclosed, they are no longer classified and no law would be broken by this action. I recommend sending it to my address at 1727 Candlestick Lane, Newport Beach CA 92660 by express mail or FedEx and I will cooperate with the mailer. Alternatively, he/she could write me first asking any questions.
In a separate interview with witness Navy yeoman Dale Bailey, he asserts that he saw a version of this Manual when he was assisting in the destruction of classified UFO material for an Admiral in 1976.
Matching the type font for a printed document can be helpful in assessing authenticity, although with sophisticated PageMaker or equivalent software available, skeptics often claim that it is too easy to fake. However, if fake, this Manual was produced before it was mailed on March 1994; the software available then was quite crude. Furthermore, Ryan Wood has shown convincingly that such an effort would have cost hundreds of thousand of dollars.
After I had a good copy of the documents, I made an appointment to visit the US Government Printing Office and met with Mr. Robert McArtor, whose job it was to answer questions of the public. This man was a many-year employee, and quite a credit to the Public Printer. He assessed the good copies I had made of the Manual, and in about an hour had concluded that the lower case font was surely Monotype Modern by examining the details of the f’s and g’s. He provided me with high quality originals of type fonts. He said that this was common in 1954. He did note some surprise that the word “federal” (as in “federal law”) in the security warning was not capitalized because that is now their custom. However, he said that he was certain that it was done on a Monotype press when he noted that there were a couple of raised “z”s in the text. He said this was an almost certain mark of authenticity because it was one of the rare errors that emerged from the old Monotype machines when the lead letters did not drop down all the way. This happened because seldom used letters like the z got some crud on a few of the brass slugs.
Slide 44 shows a high clarity comparison of the SOM 1-01 “z” in “unauthorized” and the “z” in an authentic Camera Guide (found by Ryan Wood at the Stanford Library after much hunting) in the word “synchronizer.”
There are three “intellectual” techniques (as opposed to “physical”) for authentication that apply in our case: looking for anachronisms that might not fit the alleged publication time, looking at the use of language, and comparing with known authentic documents.
In the Manual, there are two potential anachronisms, both of which have been mentioned and are noted on Slide 45. We will deal with each of these objections shortly. Slide 46 shows four examples of subtle changes in the use of language (etymology) that tends to favor the authenticity. In 1954 and earlier, First Aid was written with initial caps, and now it is lower case, changing in the late 50s. Similarly, the two-word “screw driver” was the normal way of describing the tool, but about the time that it came to represent vodka and orange juice, somehow it became one word for both meanings. Finally, Kraft tape was popularly on sale in the early 50s but now is largely replaced by duct or plastic tape. Furthermore, the word “kraft” is no longer capitalized in the dictionary, reflecting the generic use of a strong paper made of sulfate pulp.
The classic authentication process is to compare with known genuine articles, and Slide 47 provides a comparison of the cover pages of our Manual and the Technical Manual ™ that included the legitimate example of the raised “z.” Comparing with a variety of Army Field manuals of that era, Slide 48 shows the many points of similarity throughout. We have also compared the details of the printing with the instructions provided in the 1953 Style Manual for the USG Printing Office. All details check.
So, What are the Objections?
With such an overwhelming array of points of authenticity, why would anyone think SOM 1-01 not to be genuine? Well, it’s OK to be skeptical, because there have been a few examples of fake documents, and we wouldn’t want to waste a lot of time an money poring over the details of a hoaxed document. Some skeptics assume that everything is a fake and try to prove it without seriously considering the fact that if there WERE crash recoveries, once would expect there to be something to describe the process.
Overall, about twenty objections were raised, of which I have identified five as having some logical merit, and will respond to now. They are shown in Slide 49 and will be dealt with one at a time.
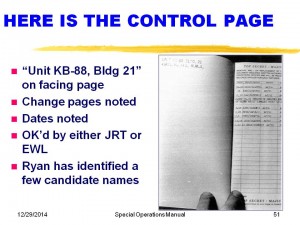
Slide 50 deals with the question of “Where is the document control?” Actually, as Don and I were making copies of the negative, there was one that was so hard to read that Don had not run a copy. When we ran the copy and studied it, there was the document control page! It showed eight entries over nearly three years replacing or removing pages from the document. Each of these actions was accompanied by a time and date typed in, with the authority of either MJ/04 or MJ/01, and the initials either EWL or JRT. Ryan Wood and I have initiated the process of identifying all the JRT and EWL names in the military in 1954 -1957 to try to locate the individuals responsible and see if they were willing to have an unclassified discussion about this now unclassified Manual.
In addition (see Slide 51), facing the control page is the back of the cover page without a security caveat, but it does have the equivalent of a control, in that it identified “Unit KB 88, Bldg. 21 from Kirtland AFB, N. MEX.” This is also significant in that the present abbreviation of New Mexico as NM for address did not occur until much later. In 1954, “N. Mex.” was common.
The answers to the “downed satellite” argument are shown on Slides 52 and 53. In the first place, the entire strategy is that of deception—it is even the title of the paragraph! Deceptive statements are not usually true. Furthermore, it was just one of five choices offered to keep nosy people away. The big argument, though, comes from those who say, “Why would anyone be impressed by a known false statement?” Actually, most people were aware of our plans for satellites in April of 1954, as a result of enormous coverage of this new space thinking. Slide 53 shows eight of many references to satellite discussions before this date, including a Time Magazine article just the previous month speculating on whether a satellite had already been covertly launched. So, satellites were on the public’s mind and “downed satellites” were a very credible concept.
The third objection raised that warrants discussion is the claim that Area 51 did not exist in 1954, and therefore the Manual must be a fake. Interestingly, early responses to the SOM 1-01 by the Air Force that claimed it to be a fake had the paragraph discussing this issued blacked out, as if it was still so sensitive they didn’t want to touch the topic. Actually, there is evidence that this facility was started in 1951, probably for the express purpose of having a good place to send the EBEs recovered. Slide 54 shows the banner of the Las Vegas Review-Journal for January 5, 1951, and the next Slide 55 shows a copy of the accompanying article describing a massive construction project of $300 million 1951 dollars. This is easily enough money to build this kind of a complex. Furthermore, accompanying the article was the testimony of a local witness of the time who described the large number of construction actions going on at the time.
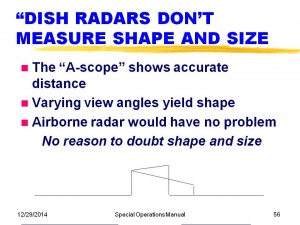
The fourth challenge was that the description of the vehicles included details on the shapes and lengths with precision not possible with 1950s kind of dish radars. Two of the shapes (cigars, triangles) specifically referred to radar as the source of the size and shape information. I worked on radar returns during my McDonnell Douglas career, so I know something about the subject. Although a dish radar puts out a rather wide angled beam, the returns from the target are quite precise in time (and thus, distance) although angles are poorly estimated. The return from the nose of the object provides the mark at one end, and the last return before the signal drops is the end of the vehicle. Two examples are shown on Slide 56, showing conceptually the “A-scope” signal strength return. If you have several measurements, especially if you do not ignore the obvious visual information, one can make quite good estimates of distances. Furthermore, the critics assume that these measurements are using ground-based radar. Aircraft had radar, too, and could have measured lengths with great accuracy. There is no reason to doubt the sizes and shapes reported in the Manual.
The final challenge was that the “Restricted” caveat on the cover page is not consistent with the use of Top Secret. Although the classification of Restricted at one time existed and was lower than Confidential, it was eliminated in about 1953. The word “restricted” can have a generic meaning too—access to this information is restricted to those who have both the clearance and the need to know. While this is officially true, the publisher of the Manual clearly thought about making it very clear than this Manual was to be of extremely limited distribution. Examples of the use of restricted together with Top Secret exist, and Slide 58 shows a great example of one: a July 14, 1954 memo from Cutler to Twining changing the meeting arrangements for an MJ-12 Special Studies Project meeting of the National Security Council. This memo came from the National Archives and is one of the few Archival confirmations of the existence of MJ-12. Its classification is “Top Secret Restricted Security Information.”
Other critics have shot at the authenticity early and often, but hardly a single critic has ever asked me for a high quality copy of the Manual. Even Don Berliner did not elect to pay for a copy at the time we originally printed the 8 x 10 glossies. Slide 59 lists some of the arguments included in an International UFO Reporter (CUFOS) article in 1996. Most of the explanations are self evident, but the last two deserve a bit of expansion. Critics claim that if the evidence is not available in the archives, that suggests that it does not exist. It is well known that the Archives have a declassification procedure that is charged with not releasing information that would be unfavorable to National Security. It should be evident to anyone that if the Government really wants to keep a secret, they would have no compunction about lying about the existence (or non-existence) of documents. Even “making them disappear” would clearly be expected.
In the history of questioned documents, there is only a trail of evidence pointing to fakery. One cannot prove they are genuine, but one can prove they are fake, using the techniques I outlined earlier. Therefore the onus in on him who claims “fake” to find the evidence for fakery, rather than to say, “You haven’t proven them to be authentic.” Failing all the tests for fakery is about as close as you can come to proving authenticity.
Other, less careful skeptics have written whole chapters and books on why MJ-12 is a hoax. See, for example, “Case MJ-12” by Kevin D. Randle, who brings forth everything that he can think of that might be favoring fake on every questioned document on this topic. A very careful reading of this book by me yields 159 marginal notes where I either disagreed with his facts or his logic. There was no significant discussion of the Special Operations Manual 1-01 or issues of fakery, a rather significant omission. Scooping up some of the fakery arguments, Slide 60 highlights the concerns and the responses. Not yet mentioned today is the criticism that the Manual states that the information “carries a security level 2 points above that of Top Secret.” Two responses: (a) maybe what they mean was that MAJIC was one point and EYES ONLY was the other. Alternatively, there may be a security system within the layers of onions, and in 1954, this was precisely right. Colonel Corso in his book “The Day After Roswell” personally described 14 layers of clearance that he had never heard of before he got them.
One other criticism on Slide 60 is that there is no security control number. This appears to be true, and is a puzzle. The best answer I can offer is one of two: (a) a control number may have been on the back of the cover or some other location not photographed; or (b) the assignment of the Manual by stamp to Unit 88, Bldg. 21, Kirtland AFB makes it the equivalent of a control. In addition, most of the critics assume that the security system being used is that of the Department of Defense. If the CIA printed this, for example, the CIA security procedures would have been those in use. Furthermore, MJ-12 could easily have been given their own authority for security, since security is clearly the predominant focus of every aspect of the program.
All these exposures to claims of fakery have led me to create one summary chart of the eight phony claims of fakery, Slide 61. The only two not touched on so far are “Why would the Government keep ETI life secret?” Slide 62 summarizes the five reasons, ANY ONE OF WHICH would have been enough to justify keeping this secret. Unquestionably, the discovery during WW2 of the Missouri crash would have focused on the technology issues. The development of technical applications would have been very easy to implement using the same procurement strategy we used for analyzing captured enemy aircraft: cover contracts, classified results, apply the technology for ten years in the military, then release it to the public via the normal patent process.
Many people also, say, “OK, but why still keep it secret TODAY?” The answers are in Slide 63. The last point about a “clear and present danger” may require some comment. Only those with deep understanding of the interaction of the alien races with out would know whether we are truly in control or not. “We” meaning our “good guys,” whoever they are. It is intuitively clear that if the aliens have begun to significantly influence our processes, it is unlikely to be good for Homo-sapiens.
In spite of the excellent arguments, there is a fine set of arguments against continued secrecy, shown in Slide 64.
Nevertheless, I still believe that our Government does have the right to keep the technology secret and to do testing of new systems at covert locations, within the Constitution. If the enforcement techniques are both illegal and unconstitutional, then we should fix that problem.
Wrapping up, having listened for 40 minutes or so to the detailed contents of the Special Operations Manual 1-01, you probably would like to buy a replica of it, available at my table in the back for just five bucks.
Conclusions
The most important conclusion for my topic is that there have been no credible and specific arguments supporting fakery. Therefore, the alternative is the conclusion that it is almost certainly genuine, based on everything you have seen or read here. If this Manual is genuine, then almost everything the Government has told us about UFOs has been deceptive, although I will concede that so few people know the true story that most of the Government people are sincere in what they say—they just don’t know!
I have two slides of conclusions based on the study of the Manual, other questioned documents and other UFO reports from witnesses. Starting with Slide 66, I conclude that several aliens species have been visiting us for years, and the two EBE Types I and II shown in the Manual are consistent with many other witness reports. There are others that were not in the Manual, from other civilizations, based on forensic language analysis of the work of Dan Young from abductees as well as worldwide occupant reports over the years.
Second, we have had success almost beyond belief in controlling the crash recoveries from becoming widespread accepted public knowledge by the media. Part of this success is probably due to direct media influence, long judged an essential issue. The secrets have been kept in spite of numerous leaks of classified documents, many of which seem to be quite authentic (and have not been proven to be fake using objective analyses), and these leaks have been expected and are controlled. Leaks have probably become less frequent because of the heavy reliance on computer-based security system that result in greater difficulty in siphoning off draft copies.
When I first began to study UFOs, it seemed to me that there was no good reason for the Government not to tell the public what was going on. I thought that the disinformation folks like Quintanilla, Menzel and maybe Hynek were the bad ones who should not have been lying to us all along. Less clear now to me what the right course of action should have been. I still believe that although people do not have the authority just because they take a security oath to commit obvious unconstitutional crimes, that we do have the right to keep this technology to ourselves in a legal manner at secret locations of our choosing. The Manual makes it clear that this is what we have been doing for nearly 50 years. How far have we come? To what extent is our society richer, the way that Harry Truman and Vannevar Bush though it might be when they decided to proceed with Operation Majestic 12? I do not know.
That leads me to the first point of Slide 67, which is that some of the smartest men of our generations have managed this program, including Vannevar Bush, Oppenheimer, Einstein and the others on the original MJ-12 Committee. They have been replaced with equally smart people as they died off. Speculating on who they are today is beyond the scope of this talk. This program has been so important that it has never lacked for money, as evidence by the $300 million 1951 dollars to build Area 51 and today’s huge black budget, further augmented today by the threat of terrorism. It is evident that we have been clearly attempting to “reverse engineer” these recovered parts and probably still are. That we have been unsuccessful in unimaginable. The only question is what percent of today’s technology can be backtracked to those of the UFOs.
Finally, although I think it would make sense if we would end the sham that none of these crashes or abductions have ever happened, I would defend the right for us to conduct Constitutional secret tests of technology and weapons at location of our choosing. However, if a legitimate arm of the U.S. Government is not controlling this program, we should regain control of it, as is our Constitutional right.
Whether the covert scientists have discovered the secrets of energy and propulsion that the UFOs use is not something I know. I used to think that they had not. Now I am less sure of that. However, I do believe that we may be approaching an understanding of the control of vacuum energy that has the prospect of benefiting all of us.